Microsoft Defender
Attach Microsoft Defender to Detect
To attach a Microsoft Defender account to Detect, you will need:
- The Prelude CLI
- An Azure user with Global Administrator role
In Azure
Create an app
Follow the official Microsoft Defender documentation to create a new app. While you walk through the guide:
- Please take note of your app's TENANT ID (step 7), APP ID (step 7), and APP SECRET (step 6)
- You do not need to create a multi-tenant app (step 8)
- This integration requires:
User.ReadMachine.Read.All
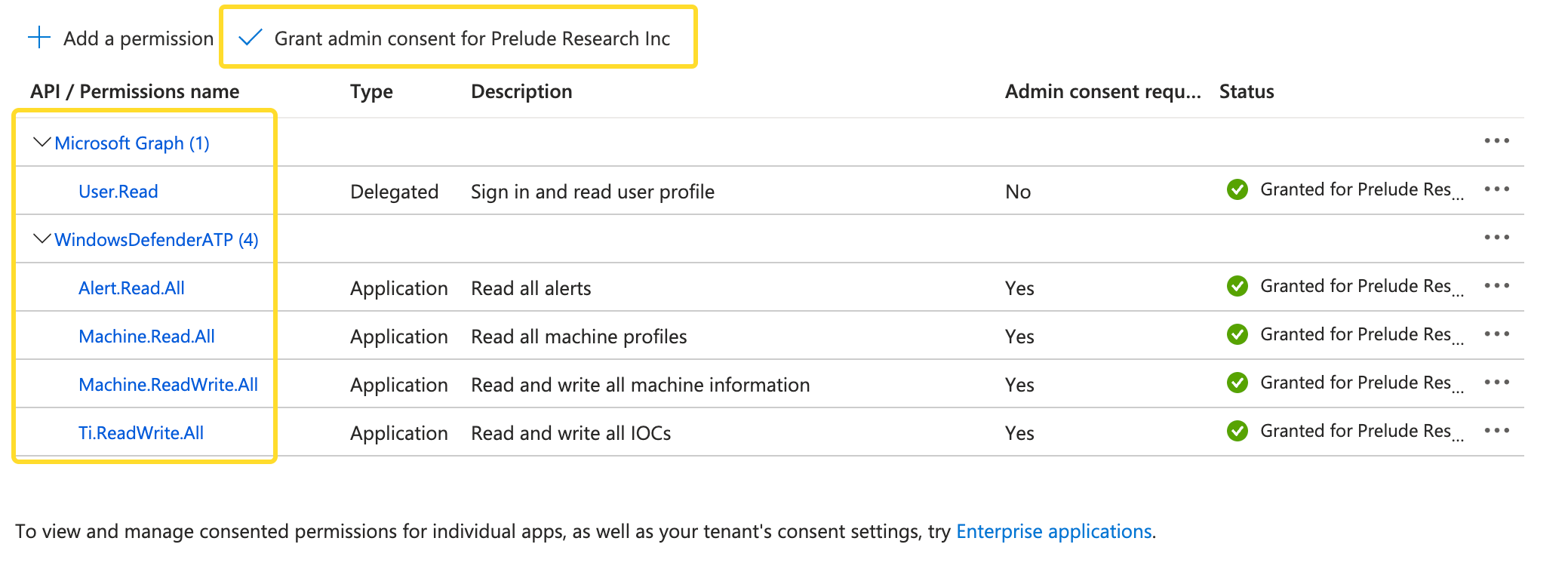
Note: After adding the above permissions ensure you click the "Grant admin consent for user" as highlighted in the screenshot below.
To see IOC's submitted via Prelude:Under the Microsoft 365 Defender portal: browse to Settings > Endpoints > Rules/Indicators (https://security.microsoft.com/preferences2/custom_ti_indicators/files).
Note: Microsoft Defender has the following requirements to enable hash/IOC blocking:
- Microsoft Defender Antivirus in active mode (Get-MpComputerStatus | select AntivirusEnabled,realtime*)
- Cloud based protection Enabled - "High" or "Higher+" required
- Defender > Endpoint > Advanced Features > https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/advanced-features?view=o365-worldwide#allow-or-block-fileAllow Or Block Files Enabled
- Antimalware client version must be 4.18.1901.x or later
- Supported OS (Win 10 v1703+, Server 2012 R2+)
In Prelude
Attach the partner via UI
- Navigate to your user name in upper right hand corner and select "Integrations"
- "Connect to Windows Defender"
- Fill out Base URL, Tenant ID, APP ID and App Secret to connect
Attach the partner via CLI
Run the following command to attach the partner
prelude partner attach defender --user <TENANT_ID> --secret <APP_ID>/<APP_SECRET> --api <HOST>
--apiis an required field that should be set tohttps://api.securitycenter.microsoft.com. Optionally can be set to hit one of Microsoft's regional endpoints, examplehttps://api-<REGION>.securitycenter.microsoft.com
Your account credentials are stored, encrypted at REST, behind the Prelude Service API.
After attachment, the Prelude Service will send your Defender account a new IOC every time a probe reports a test in the UNPROTECTED state. Following this report, Defender should start catching the test.
Detach the partner via UI
-
- Navigate to your user name in upper right hand corner and select "Integrations"
- "Disconnect Windows Defender"
Detach the partner via CLI
To detach the partner from your account, run:
prelude partner detach defender
Updated 3 months ago
